Reduce Risk
We focus on detecting malware and high risk content in documents arriving every day as email attachments. Stop breaches before they happen.
QuickSand Framework
![]()
QuickSand is an analysis framework to analyze suspected malware documents to identify exploits in streams of different encodings or compressions. QuickSand supports documents, PDFs, Mime, Postscript and other common formats. Unlike antivirus, QuickSand is a designed to dig deeper than typical antivirus and detect threats despite obfuscation, nested compression and encryption.
The culmination of over 10 years of malware forensic tool technology that has been the goto for malware analysts is now available as a cross platform Python-based module.
Features
-
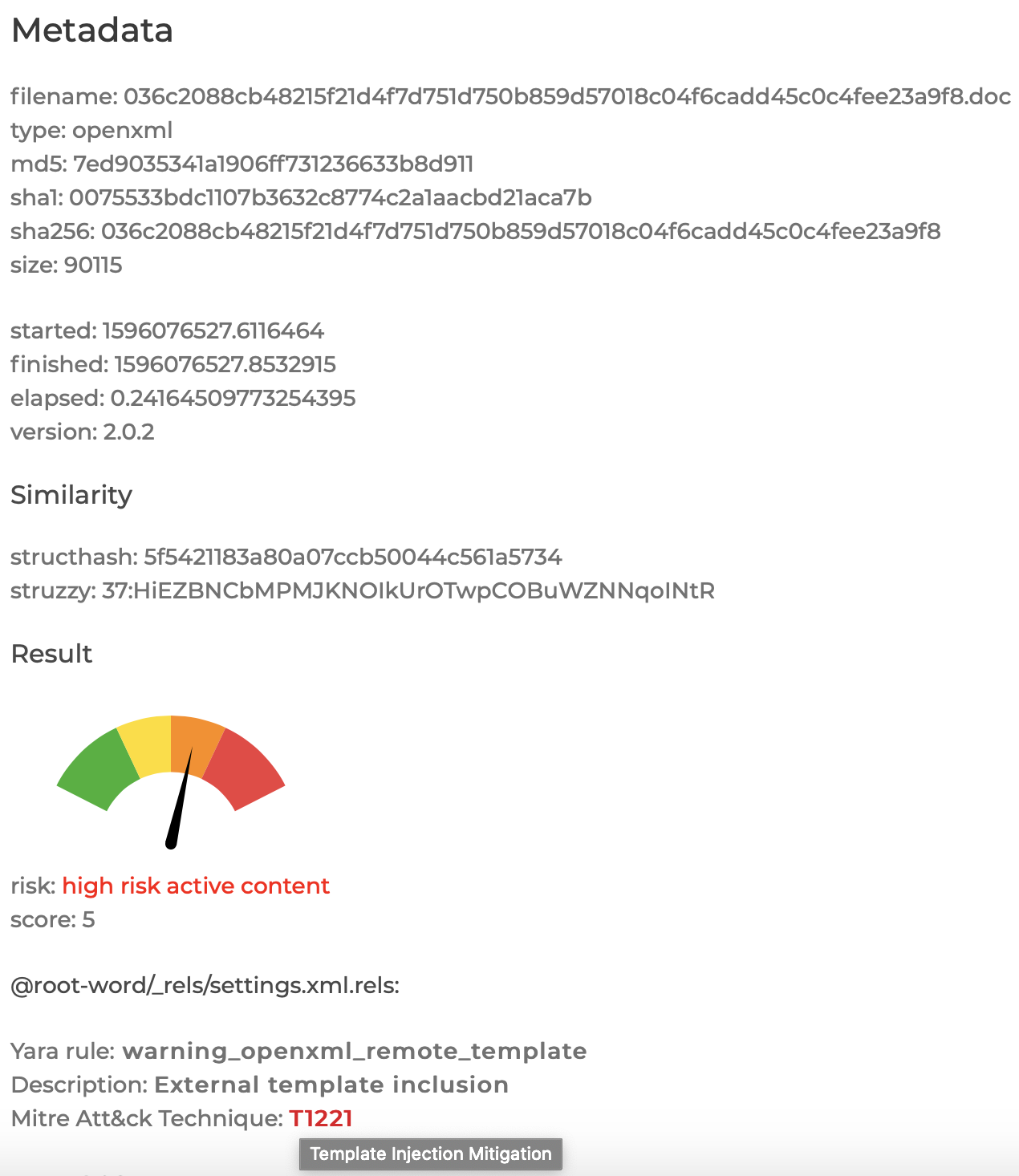
Decode and decompress streams in OLE (Microsoft Word doc/Excel xls/Powerpoint ppt), OpenXML (Word docx/Excel xlsx/Powerpoint pptx), Hangul HWP, Adobe Reader PDF, Rich Text Format RTF, Postscript, Mime Emails, MSO, Adobe XML Data Package .XDP PDF.
-
Scan with Yara within streams and sub-files.
-
Detect active content such as ActiveX, VBA, Macros, JavaScript, Shell commands.
-
Detect and define CVE ID for known exploits.
-
Define Mitre Att&ck framework technique IDs for each exploit.
-
Handle nested formats, some encryption and nested encapsulation.
-
Includes Python module updates and exploit signature updates.
Use Cases
-
Detection: QuickSand can dig deeper into document streams and encodings to detect malware normal AV may miss.
-
Reduce Risk: Detect active content that could access private information within your organization.
-
Threat Intelligence: Use QuickSand’s similarity features to identify documents from the same actors or exploit kit. Define attribution through TTPs.
-
Save Time: Use QuickSand results to determine the CVE vulnerability corresponding to the version or Office or PDF software to use in a Dynamic Sandbox to achieve exploitation so that network IOCs can be extracted.
-
Common Language: Determine exploits by CVE and Mitre Attack Techniques to map your adversary’s TTPs quickly and efficiently.
Try QuickSand Free
Try scanning a Document or PDF
Contact us to order.